The regulatory countdown that defense contractors have been watching for years is finally over. On November 10, 2025, the Department of Defense began including CMMC 2.0 requirements in contract solicitations - transforming cybersecurity compliance from a policy goal into a binding contractual obligation for anyone in the defense supply chain. If you manufacture components for the DoD, provide engineering services, or operate anywhere in the defense industrial base, CMMC 2.0 compliance now directly determines whether you can bid on and win contracts.
Read MoreKey Innovations and Insights from the Heart of Microsoft HQ
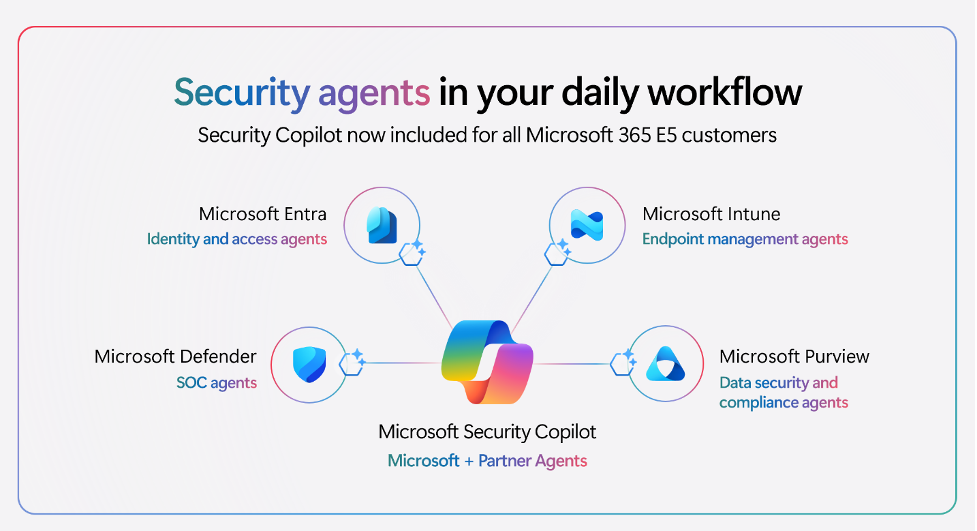
Microsoft Security Engineering Airlift is an exclusive, invitation‑only event designed to bring together Microsoft’s top engineering teams with a select group of their most strategic and technically advanced partners. A group of my Daymark colleagues and I had the privilege of attending this event for an opportunity to gain unprecedented access to product groups, roadmap insights, and advanced security engineering guidance directly from the teams that build Microsoft’s cybersecurity technologies.
At the core of Microsoft Security’s mission is a powerful motto: “Make the world a safer place for all.” This vision guided the 2026 Microsoft Security Engineering Airlift, held at Microsoft headquarters, as we explored the latest advancements in protecting our digital world. The central theme of the event focused on the dual commitment to security for AI and AI for security, recognizing that artificial intelligence serves both as a powerful tool and a critical asset that must be protected.
Read MoreComparing Common Approaches to GCC High Migration
Introduction
Organizations that work with U.S. government contracts or handle sensitive regulated data often face tough decisions about their cloud strategy. Two common approaches for meeting requirements are migrating all users to a dedicated Microsoft GCC High tenant or creating a secure enclave and migrating only select users. This blog post explores the differences between these two strategies, highlighting the pros and cons of each so you can make an informed decision for your organization.
What Is GCC High?
Microsoft GCC High (Government Community Cloud High) is a dedicated cloud environment designed specifically for U.S. government agencies and contractors that must comply with strict regulatory standards, such as FedRAMP High, ITAR, and DFARS when handling controlled unclassified information (CUI). GCC High provides enhanced controls, data residency in the continental United States, and a dedicated infrastructure that separates government data from commercial environments.
What Is a Secure Enclave?
Read MoreWhy Relying on Native Microsoft 365 Protection Isn’t Enough
As more organizations transition to Microsoft 365 (M365) for email, collaboration, and file storage, it’s easy to assume that your data is fully protected in the cloud. However, relying solely on Microsoft’s native capabilities could leave your business vulnerable to data loss, human error, and cyber threats. In this blog post, we’ll explore five compelling reasons why investing in a dedicated M365 backup solution is essential for safeguarding your business-critical information.
1. Microsoft Does Not Natively Back Up Your Data
Read More
As organizations continue to prioritize data governance, compliance, and information protection, Microsoft Purview has emerged as a powerful suite of tools to meet these needs. But not all Purview capabilities are created equal.
In this article, we’ll break down the primary differences between Microsoft 365 E3 and Microsoft 365 E5 Purview features, helping you understand what’s available out-of-the-box with E3 and what additional value E5 brings to the table.
Baseline Capabilities with E3
Read MoreMicrosoft has introduced Microsoft 365 Business Premium for GCC High, a tailored solution for small and mid-sized organizations in the Defense Industrial Base (DIB). This offering provides a cost-effective path to compliance with CMMC 2.0 and NIST 800-171, while maintaining the strict security and sovereignty standards of the GCC High environment.
✅ What Does GCC High Business Premium Include?
The new Business Premium for GCC High license mirrors much of the functionality of the commercial Business Premium suite but operates within Microsoft’s U.S. Government Community Cloud High (GCC-High) environment. Key features include:
Read MoreOver 50% of all IT budgets moving forward will be allocated to AI, with 60% of IT time dedicated to focusing on it. Is your IT team prepared for this significant shift in the IT landscape? Balancing support for current applications while building a future-ready platform is critical. But how can you ensure the significant investments you’re making now won’t need to be repeated in just a few years?
Legacy storage just can’t handle modern demands. It wasn’t designed for hybrid, AI-driven operations. The result? Gaps in performance, security, and cost control that put your business at risk.
Read MoreMicrosoft is introducing a new detection capability in Microsoft Defender for Office 365 to help protect your organization from a growing threat known as email bombing. This form of abuse floods mailboxes with high volumes of email to obscure important messages or overwhelm systems. The new “Mail Bombing” detection will automatically identify and block these attacks, helping security teams maintain visibility into real threats.
Email bombing is a tactic to hide important emails by flooding your inbox with irrelevant ones. For instance, an attacker might order expensive items using your Amazon account and bury the confirmation emails. If you own a domain, they could be trying to transfer it. They may also hide transaction confirmations if they accessed your bank or financial accounts. Ultimately these attacks are designed to distract you, the target, from the “real” email they do not want you to see.
Read MoreIn today's threat landscape, identity is the new perimeter—and for most organizations, Microsoft Active Directory (AD) and Entra ID (formerly Azure AD) are that perimeter. When compromised, these systems expose everything: users, access, applications, and core business operations. For CISOs and IT leaders tasked with securing and sustaining identity services, traditional recovery methods often fall short—too slow, fragmented, or insecure for today's hybrid enterprises.
Rubrik’s Hybrid Identity Recovery delivers the speed, visibility, and resilience modern organizations require, enabling businesses to bounce back quickly from ransomware, insider threats, or operational failures—without reintroducing risk.
The Threat Landscape is Escalating:
Read MoreMicrosoft is making changes to their Secure Future Initiative (SFI) and the principle of “Secure by Default.” The updates to Microsoft 365 default settings will strengthen your tenant’s security and meet essential benchmarks. These changes focus on addressing vulnerabilities associated with outdated authentication protocols and app access permissions that could increase risks to organizations.
When this will happen:
These changes will begin rolling out in mid-July 2025 and are expected to be completed by August 2025.
How this affects your organization
The following settings will be updated:
Read MoreSubscribe to Daymark Insights
Latest Posts
Browse by Tag
- Cloud (70)
- Microsoft (47)
- Security (47)
- Azure (36)
- Data Protection (32)
- Partners (32)
- Data Center (28)
- Backup (26)
- Compliance (24)
- Daymark News (23)
- Data Governance (20)
- Storage (20)
- CMMC (18)
- Veritas (18)
- Virtualization (18)
- Cybersecurity (17)
- Cloud Backup (14)
- Disaster Recovery (14)
- Government Cloud (14)
- Managed Services (13)
- GCC High (10)
- Featured Gov (9)
- Industry Expertise (9)
- AI (8)
- Networking (6)
- Hybrid Cloud (5)
- NIST SP 800-171 (4)
- Reporting (3)
- Services (3)
- Cloud Security (2)
- Copilot for Microsoft 365 (2)
- GDPR (2)
- Pure Storage (2)
- Mobile (1)
- Reporting-as-a-Service (1)





.png)






