The regulatory countdown that defense contractors have been watching for years is finally over. On November 10, 2025, the Department of Defense began including CMMC 2.0 requirements in contract solicitations - transforming cybersecurity compliance from a policy goal into a binding contractual obligation for anyone in the defense supply chain. If you manufacture components for the DoD, provide engineering services, or operate anywhere in the defense industrial base, CMMC 2.0 compliance now directly determines whether you can bid on and win contracts.
Read MoreKey Innovations and Insights from the Heart of Microsoft HQ
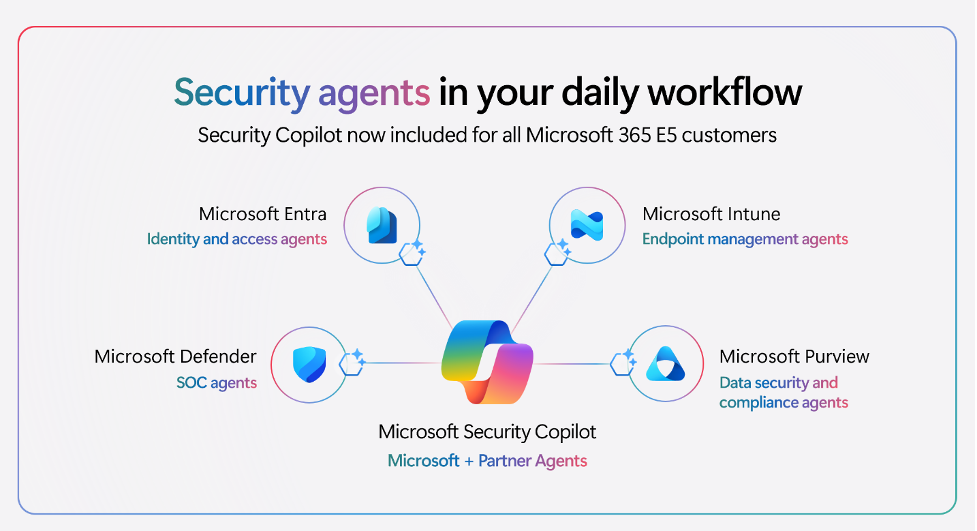
Microsoft Security Engineering Airlift is an exclusive, invitation‑only event designed to bring together Microsoft’s top engineering teams with a select group of their most strategic and technically advanced partners. A group of my Daymark colleagues and I had the privilege of attending this event for an opportunity to gain unprecedented access to product groups, roadmap insights, and advanced security engineering guidance directly from the teams that build Microsoft’s cybersecurity technologies.
At the core of Microsoft Security’s mission is a powerful motto: “Make the world a safer place for all.” This vision guided the 2026 Microsoft Security Engineering Airlift, held at Microsoft headquarters, as we explored the latest advancements in protecting our digital world. The central theme of the event focused on the dual commitment to security for AI and AI for security, recognizing that artificial intelligence serves both as a powerful tool and a critical asset that must be protected.
Read MoreMicrosoft is introducing a new detection capability in Microsoft Defender for Office 365 to help protect your organization from a growing threat known as email bombing. This form of abuse floods mailboxes with high volumes of email to obscure important messages or overwhelm systems. The new “Mail Bombing” detection will automatically identify and block these attacks, helping security teams maintain visibility into real threats.
Email bombing is a tactic to hide important emails by flooding your inbox with irrelevant ones. For instance, an attacker might order expensive items using your Amazon account and bury the confirmation emails. If you own a domain, they could be trying to transfer it. They may also hide transaction confirmations if they accessed your bank or financial accounts. Ultimately these attacks are designed to distract you, the target, from the “real” email they do not want you to see.
Read MoreMicrosoft is making changes to their Secure Future Initiative (SFI) and the principle of “Secure by Default.” The updates to Microsoft 365 default settings will strengthen your tenant’s security and meet essential benchmarks. These changes focus on addressing vulnerabilities associated with outdated authentication protocols and app access permissions that could increase risks to organizations.
When this will happen:
These changes will begin rolling out in mid-July 2025 and are expected to be completed by August 2025.
How this affects your organization
The following settings will be updated:
Read MoreIs your organization ready to modernize its security operations with Microsoft Azure Sentinel — but unsure where to start? Whether you're just beginning your Sentinel journey or looking to maximize your existing investment, Daymark’s expert-led Proof of Concept (PoC) provides the hands-on experience and technical guidance you need.
Protecting your organization from sophisticated cyber threats requires more than isolated tools and fragmented systems. Microsoft Azure Sentinel — a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solution — offers a unified approach to modern security operations — but success depends on knowing how to deploy and use it effectively.
Read MoreIs your organization struggling to balance mobile security with employee productivity? Are you confident that only secure, compliant devices can access your business applications? You are not alone. In today’s hybrid and mobile-first work environment, organizations face the challenge of securing corporate data while ensuring employees can work efficiently from anywhere. Without a comprehensive mobile device management (MDM) solution, companies risk data breaches, unauthorized access, and compliance violations.
Daymark’s Microsoft Intune Workshop
Daymark is here to help. With our Microsoft Intune Workshop, your organization can learn how to gain complete control over mobile security, streamline IT operations, and empower your workforce with seamless and secure access to business applications—no matter where they work.
Read MoreDMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication, policy, and reporting protocol. It builds on the widely deployed SPF and DKIM protocols, adding linkage to the author (“From:”) domain name, published policies for recipient handling of authentication failures, and reporting from receivers to senders to improve and monitor the domain’s protection from fraudulent email.
DMARC is designed to fit into an organization’s existing inbound email authentication process. The way it works is to help email receivers determine if the purported message “aligns” with what the receiver knows about the sender. If not, DMARC includes guidance on how to handle the “non-aligned” messages. Because cyber security continues to be a top priority for businesses, DMARC adoption is on the rise for several good reasons.
Top 3 Reasons to Implement DMARC
Read More
The risk of a ransomware attack continues to increase at a frightening triple-digit annual growth rate. How bad is it? Bad, really bad. Businesses based in the U.S. face an 80% chance of an attack, compared to 31% chance in EMEA and 9% in the Asia-Pack region. As the attackers’ sophistication increases and cybergangs are forming, it is important to understand what the attackers are going after and how to increase your ransomware resilience.
Ransomware Demand and Payment Trends
- In 2022, companies with $10 million in revenue or less had an average payout of $690,9961
- Large enterprises (revenue of $5 billion plus) took a bigger hit, with an average $2,464,3392 ransom payout
- Recent ransom demands have been as high as $30 million with payouts that have exceeded $8 million
- Threat actors are increasingly focused on extortion techniques—often layering them on top of each other
- Harassment is another extortion tactic being used in more ransomware cases. Ransomware threat actor groups will target specific individuals in the organization, often in the C-suite, with threats and unwanted communications3
- Cybercriminals threatened to leak stolen data in about 70% of ransomware cases involving negotiation in late 20224
- The United States is still the most severely impacted, accounting for 42% of the observed leaks in 20225
- As of late 2022, threat actors engaged in data theft in about 70% of cases compared to 40% in mid-20216
Don’t Count on the Government for Help
Read MoreEnsuring cybersecurity for an enterprise is a job that is never done. It’s a challenge that requires constant vigilance and, in recent years, has been exacerbated by low visibility into highly distributed and dynamic cloud data spread across increasingly fragmented environments. Our trusted cybersecurity partner, Rubrik, has taken another step to enhance cyber security by acquiring Laminar, a leading data security posture management (DSPM) platform. It’s a strategic move that results in Rubrik’s ability to offer customers a complete cyber resilience offering that reduces weaknesses in an organization’s security strategy.
Securing cloud data is different from securing your infrastructure. Businesses have innovated the way they use cloud data, but not the way they secure it. Not only do you need a data-centric tool for the job, you also need an agile, cloud-based approach to keep up with the dramatic expansion and replication of data manipulated by developers and data scientists so that they can leverage data for innovation without increasing exposure or data protection risks.
Read MoreAzure Sentinel is a cloud native Security Information Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) solution from Microsoft. It was the topic of discussion at one of our recent Daymark Cloud Clinics where our technical cloud consultants offer complimentary technical training and tips on a wide range of Azure and Office 365 features.
Read MoreSubscribe to Daymark Insights
Latest Posts
Browse by Tag
- Cloud (70)
- Microsoft (47)
- Security (47)
- Azure (36)
- Data Protection (32)
- Partners (32)
- Data Center (28)
- Backup (26)
- Compliance (24)
- Daymark News (23)
- Data Governance (20)
- Storage (20)
- CMMC (18)
- Veritas (18)
- Virtualization (18)
- Cybersecurity (17)
- Cloud Backup (14)
- Disaster Recovery (14)
- Government Cloud (14)
- Managed Services (13)
- GCC High (10)
- Featured Gov (9)
- Industry Expertise (9)
- AI (8)
- Networking (6)
- Hybrid Cloud (5)
- NIST SP 800-171 (4)
- Reporting (3)
- Services (3)
- Cloud Security (2)
- Copilot for Microsoft 365 (2)
- GDPR (2)
- Pure Storage (2)
- Mobile (1)
- Reporting-as-a-Service (1)