
A CISO Primer on Navigating Cyber Insurance
After 10+ years of working with clients to negotiate and place cyber insurance, I’ve noticed that one of the most frequent challenges has always been getting the underwriters and my client’s information security stakeholder (like a CISO or CIO) to understand each other. It’s no surprise that insurance is *gasp* slow to evolve – but in their defense, underwriters have come a long way over the last three years. It’s also no secret that being a CISO is one of the most important leadership roles within a company these days. So why are there massive communications disconnects? Why are CISO’s often ill equipped (through no fault of their own) to navigate the cyber insurance ecosystem? How are brokers and their underwriting partners not ensuring that their clients understand the coverages within cyber policies and how the insurance contracts work? How can we bring all the stakeholders in the process together to make our clients more resilient and create a sustainable cyber insurance marketplace? This blog aspires to demystify cyber insurance for all the information security stakeholders in the room so that they are best equipped to dovetail their strategy with what the insurance marketplace is looking for.
Cyber Insurance Players
First, let’s outline who the main players are within the cyber insurance ecosystem:
- Policyholder and Stakeholders
- Risk Manager - manages insurance buying process and usually reports to finance
- General or Chief Privacy Counsel - manages the company’s data privacy strategy and is a great resource for helping contextualize the regulatory landscape
- Broker
- Represents YOU and your company’s interests in the insurance marketplace
- Does not always control coverages, capacity, or market appetite but their fiduciary obligation is to you
- Insurance Company
- Works with your broker to quote terms and conditions and will compete for your premium dollars in exchange for coverage
- Determines policy terms, conditions, pricing, and exclusions
- Vets and works with Incident Response (IR) firms and breach coaches to provide best possible incident response to policyholders
- Will (usually) govern the incident response costs payment and defense indemnity
- Incident Response Vendors
- Pre-approved privacy law firm “project manages” the data incident
- Digital forensics and incident response firm investigates the matter and (if needed) manages the ransomware incident
- Most policies require vendors be “on panel” or “pre-approved” by the insurer (more on this later)
An Inside Look at a Cyber Insurance Policy
Now that we’ve outlined the main players in the space, let’s look into the cyber policies themselves and outline what is included in base language. Cyber policies are usually offered with BOTH first party and third party coverages. The first party coverages are there to help the policyholder “put the fire out” and manage incident-related expenses. Third party liability coverage provides defense costs and damages to third party claimants including regulators and clients.
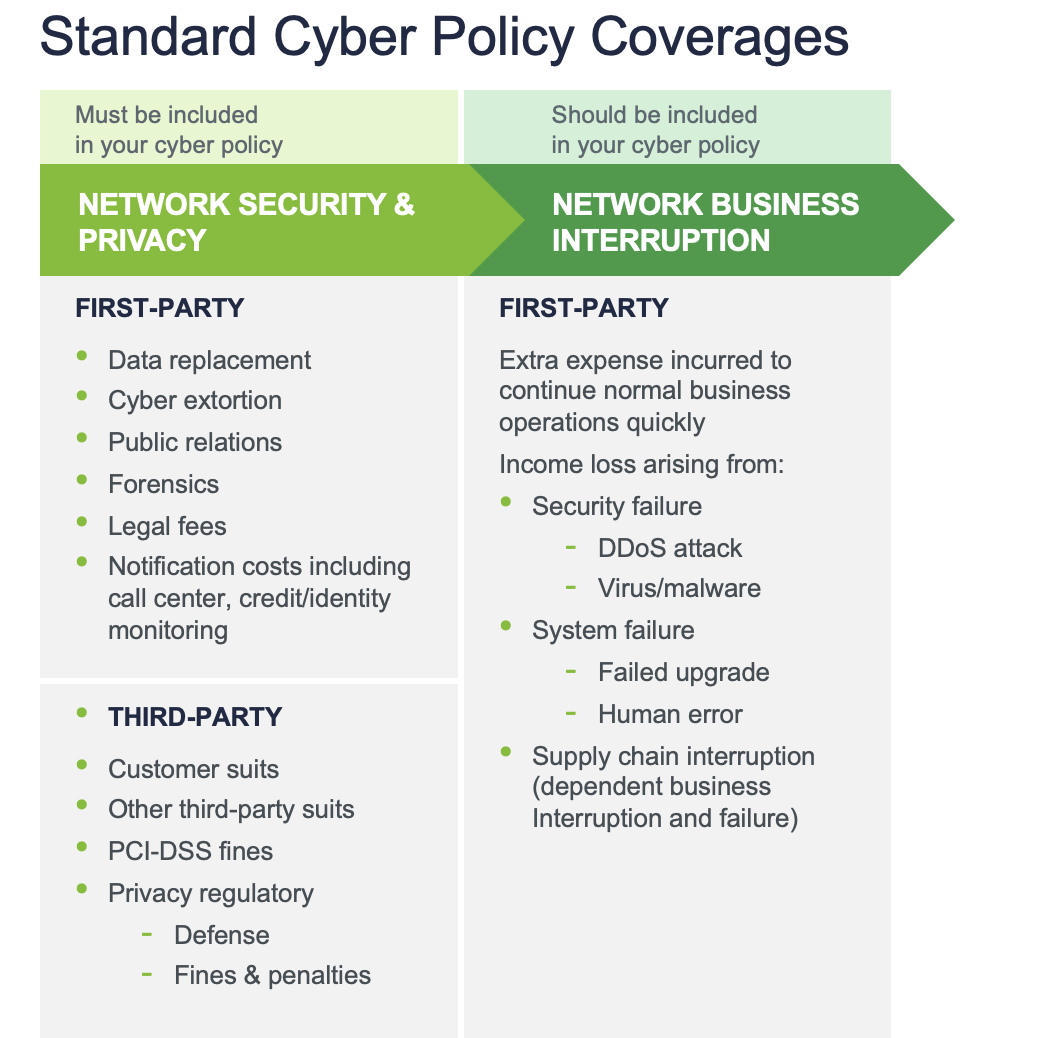
Understanding the Fine Print
With a baseline of both the ecosystem and the coverage, what can CISOs do to maximize the value of their engagement with their risk manager, broker, and underwriters?
- Understand that binary “Yes/No” applications often do not capture the entire story. A box checked on an application without any further explanation can hurt your company when being underwritten or be held against you as a misrepresentation after a claim. For example, if the application asks if you have EDR deployed across your enterprise, you should assume the underwriter means “across 100% of the enterprise” and as such, any deviation from that representation may be a problem during the claim. It’s ALWAYS better to ask a follow up question or seek clarity BEFORE signing the insurance application.
- Know who your insurance company’s pre-approved vendors are. Do you have an existing retainer with a cyber security firm? Furthermore, are you expecting to use them to help with an incident? If your insurer doesn’t know about it and that company isn’t on panel, you will likely have to seek approval after the claim happens – resulting in invaluable time lost negotiating in the midst of a crisis. Same goes for your general counsel – if they want a specific law firm to project manage the incident, they need to cross-check the policy or seek an endorsement adding the firm to the policy.
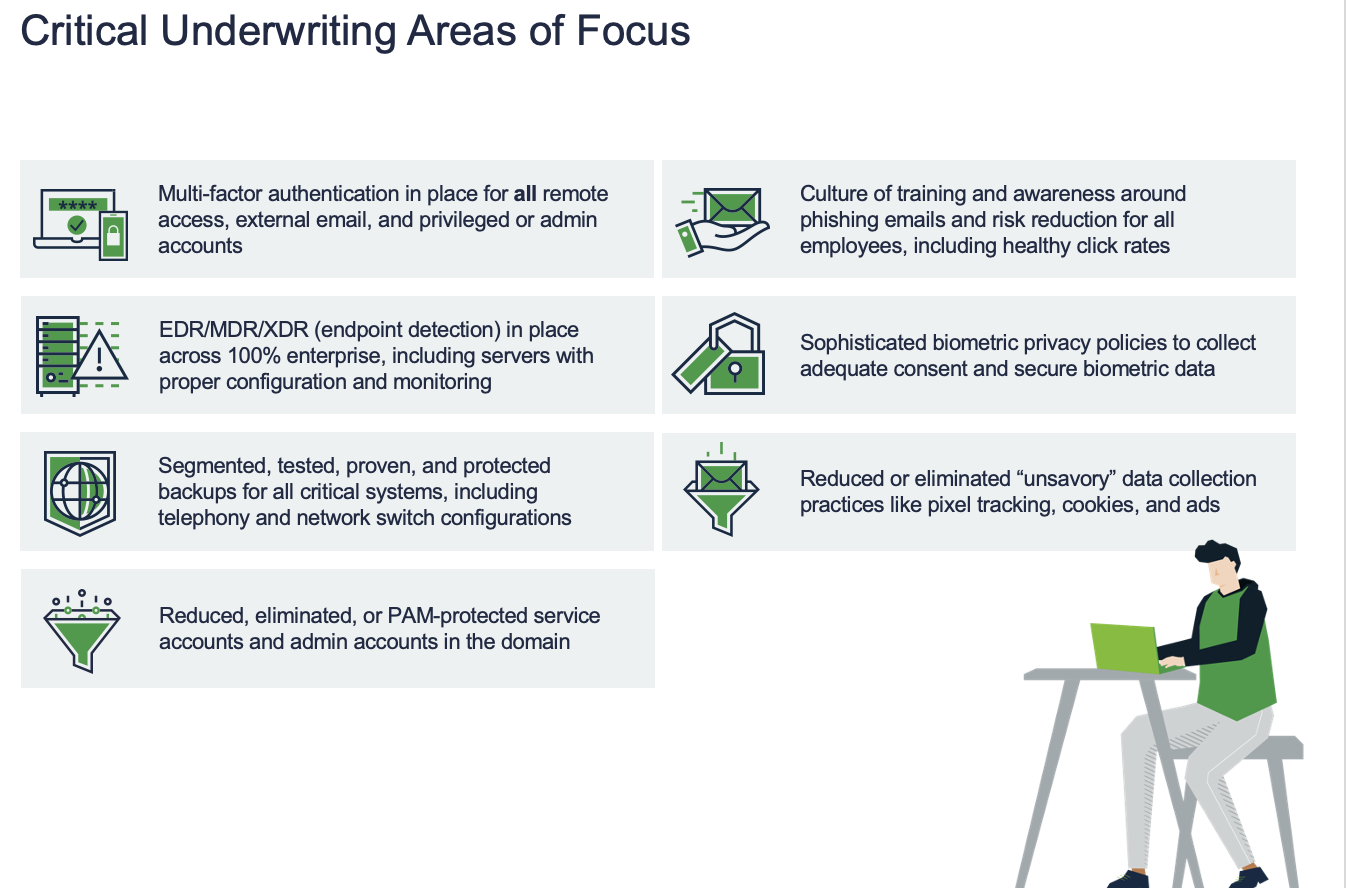
- Understand that there are certain controls that are no longer negotiable and need to be largely in place and deployed if you hope to avoid onerous deductibles, ransomware exclusions, and high premiums. Those include the critical areas of focus below:
Maximizing Your Coverage
There are several critical things that you can do to maximize your coverage, including but not limited to the following:
- Leverage your insurance company’s risk reduction and pre-breach service offerings. Most carriers offer numerous value-add services including tabletops, access to templates, and policy reviews to their policyholders. The services usually materially increase in value if you’re spending 6 figures or more in premium.
- Understand your policy. Read it and pay attention to the definitions and exclusions. Does the definition of “Insured Computer System” adequately reflect your company’s footprint? Are there exclusions related to ransomware or sunsetted software? Fundamentally, the four walls of the policy will govern the contract ONLY; and absent any bad faith on the side of your broker or underwriter, it is aways your responsibility to understand your insurance policy. If you don’t understand it, ask your broker to spend an hour going through the policy with you. It may change the game in terms of understanding what to do in the event of a claim and how to access coverage.
- Generally speaking, you should also be wary of the following exclusions as they are not necessarily something you need to accept on your policy:
- Excluded claims arising out of unsettled or unsupported software
- Excluded claims arising out of a failure to maintain the security posture declared at the point of binding
- Broad-reaching systemic or widespread event exclusions
- Cyberattacks resulting from a failure to implement a specific patch or security fix
- Wrongful data collection, failure to delete, or other elevated privacy statute-related claims
- Exclusions for claims or suits arising out of wrongful collection or wiretapping
- Exclusions for biometric claims and class action suits
This is about as fundamental of a cyber insurance primer I could fit into 1,000 words. But I will close out with one final point. It is your broker’s job to help you understand your policy and provide you guidance on how to be a better risk. Your broker should be educating you on what responses in your underwriting submission resulted in demerits and what responses were strengths. It is ABSOLUTELY your broker’s job to stand by you in the event of a claim and advocate on your behalf to the underwriter for quick and fair claims payment. And finally, (and I think sometimes brokers fall short of this), your broker should champion you in front of your stakeholders. Cyber insurance spend SHALL NOT compete with information security spend. Insurance is the last resort for your company in the event of a cyberattack. Preparation, practice, and resilience continue to be the best way to reduce cyber risk, and your broker should help communicate that message to your internal stakeholders alongside you. Whether we like it or not, we are all in this together – nobody wants to be the next victim of a cyberattack…
About the author: David Anderson is a dedicated and fierce advocate for his clients focusing on complex cyber, privacy, technology, and professional liability issues. With extensive experience in risk assessment, pre-breach network security risk discovery and risk management, as well as hands-on post-incident client support and claims advocacy, David is committed to helping his clients navigate a complex and ever-changing cyber and professional liability insurance marketplace to ensure they achieve market-leading coverage terms and conditions at the best possible premium.
David B. Anderson, CIPP/US, Vice President, Cyber, Woodruff Sawyer



