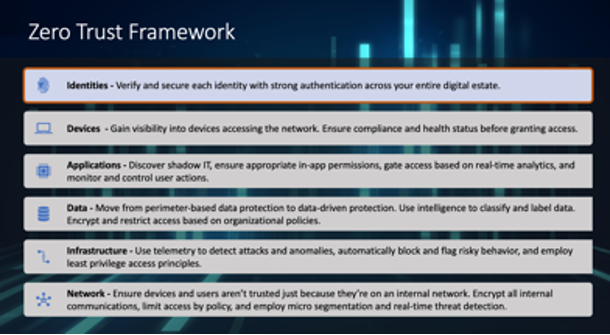
Properly securing assets is a constant challenge for IT. Staying one step ahead of the bad actors is a never-ending job and with a well-known shortage of IT security professionals, it’s critical that those of us responsible for protecting systems, networks and data are smart about deploying tools that will help remediate or minimize cybersecurity risks. Microsoft built Azure Security Center to help. It aligns Azure resources with Microsoft best practices to mitigate risks associated with security vulnerabilities that could lead to a breach or other security incident.
Microsoft Security Quick Facts
Read More