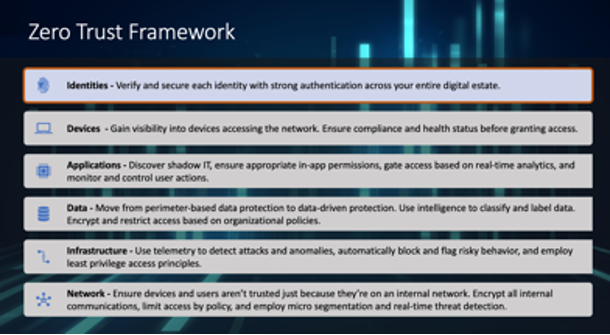
As COVID forced organizations around the world to send their workforce home, creating the work from home (WFH) phenomenon, IT and security teams rapidly focused on Zero Trust approaches to security to mitigate challenges of enabling secure remote work. Modern workplace employees are getting their work done any way they can these days – using personal devices, sharing data through new services, maxing out home WiFi, and collaborating outside the confines of traditional corporate network security. It has created an IT balancing act between security and WFH productivity.
Read MoreSecure access to email and other business productivity tools continues to be a top priority for IT administrators. Microsoft services, such as Azure Active Directory and Office 365, use OpenID Connect for authentication and OAuth 2.0 for authorization. Here’s how that process works: When Outlook connects to Exchange Online, the API requests are authorized using OAuth 2.0 Access Tokens. They are valid for one hour. When the tokens expire, the Outlook client is redirected back to Azure AD to refresh them. This provides an opportunity to re-evaluate policies for user access. If a user has been disabled in the directory or because of a Conditional Access policy, the admin might choose not to refresh the token.
Read MoreTo say the cybersecurity community is a buzz over the recent news of the highly-sophisticated data breaches at many U.S. government agencies this month due to vulnerabilities in the SolarWinds Orion IT management platform is an understatement. Experts believe that Russian government hackers are behind this global espionage which may have started as early as last spring. The threat actors conducted a supply chain attack on SolarWinds Orion Platform with a backdoor through a FireEye software update. The SolarWinds versions impacted are 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1. Agencies affected include the Pentagon, the Department of Homeland Security and the Department of the Treasury.
Read MoreI haven’t met an organization yet that isn’t interested in saving money and optimizing their cloud spend. That’s where Azure Reserved Instances (RIs) come in. Properly leveraged, Reserved Instances, particularly Virtual Machine Reserved Instances can result in some significant savings. In fact, it was the topic of discussion at one of our recent Daymark Cloud Clinics where our technical cloud consultants offer free technical training and tips on a wide range of Azure and Office 365 features.
Read More
Mimecast held their 2020 Cyber Resilience Summit remotely this year covering a wide range of topics. You can read our previous blog “Mimecast Cyber Resilience Summit 2020 – Key Takeaways” for those highlights. In addition, Mimecast provided some alarming data on the pandemic threat reality that we are facing.
Mimecast collected 100 days of detection data from January 2020 to April 2020. The results below reveal a 36.9% INCREASE in threat detections, where the key focus of threat actors has become high volume Spam and Impersonation. Here’s the breakdown:
Read More
Mimecast held their 2020 Cyber Resilience Summit remotely this year, providing some interesting updates to their suite of cyber security tools. As a leading Email Security Gateway, Mimecast has expanded their portfolio over the last few years into a more robust and comprehensive framework that they have dubbed “Email Security 3.0”.
The Email Security 3.0 Framework can be broken out into three zones of protection:
Zone 1: Perimeter – This is your traditional email delivery path and is saturated with relentless attacks. In order to protect against these threats, Mimecast leverages their advanced Targeted Threat Protection including impersonation protection, attachment sandbox, and URL Protection.
Read MoreOn July 16, 2020, the European Court of Justice (ECJ – the EU’s high court) invalidated the EU-US Privacy Shield Framework as a potential mechanism for meeting the GDPR's cross-border personal data transfer restrictions.
Effective immediately, U.S. companies that process EU “personal data” can no longer rely on registration under the Privacy Shield and must establish an alternative legal basis for any continued EU-US transfers.
Previously, cross-border transfers to the US were permitted under three mechanisms: 1) the Privacy Shield (http://privacyshield.gov), 2) Standard Contractual Clauses (SCC), and 3) Binding Corporate Rules (BCR).
Read MoreConditional Access in Azure AD provides a level of security required to maintain appropriate controls over who can access confidential and privileged information. It was the topic of discussion at our most recent “Ask the Engineer Q&A Roundtable” where attendees learned tips for a successful Conditional Access deployment and got answers to their specific questions.
Read MoreIt’s a crazy time out there. Businesses have been mandated by state governments to enable employees to work from home. Literally overnight, there have been massive shifts to connect people remotely. Suddenly even your grandparents know what Zoom is!
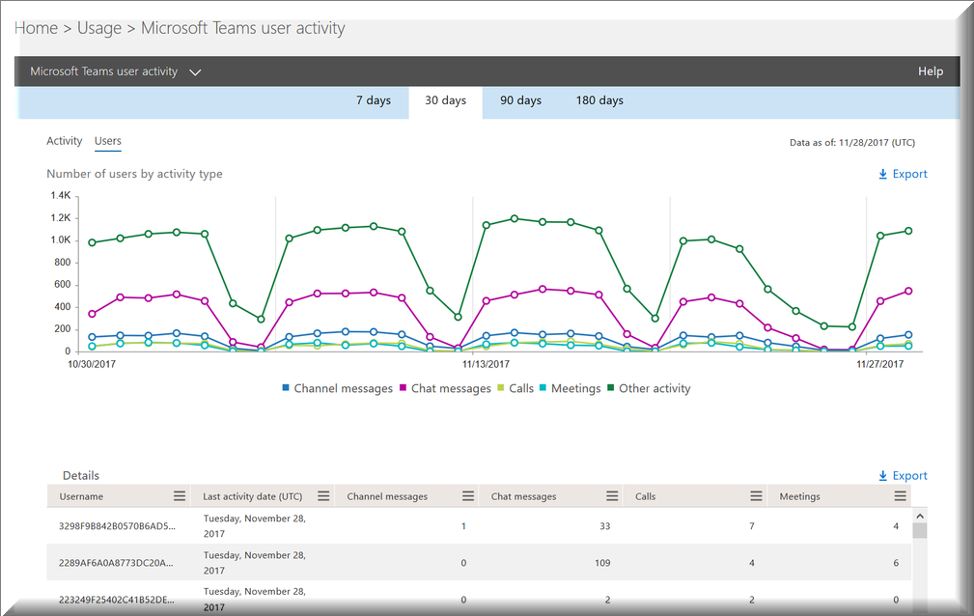
Microsoft Teams is playing an integral part in facilitating remote communication and collaboration. Most companies with Office 365 subscriptions already have licenses for this product, but just now are really rushed to enable Teams for the massive increase of remote workers.
Read MoreAs we all strive to adjust to the changes that coronavirus has brought to our lives in the past several weeks, I wanted to share some tips about self-care and coping in these uncertain times. Here are a few tips and suggestions for managing stress and staying balanced:
Read MoreSubscribe to Daymark Insights
Latest Posts
Browse by Tag
- Cloud (70)
- Microsoft (46)
- Security (46)
- Azure (36)
- Data Protection (32)
- Partners (32)
- Data Center (28)
- Backup (26)
- Compliance (23)
- Daymark News (23)
- Storage (20)
- Data Governance (19)
- Veritas (18)
- Virtualization (18)
- CMMC (17)
- Cybersecurity (17)
- Cloud Backup (14)
- Disaster Recovery (14)
- Government Cloud (13)
- Managed Services (13)
- GCC High (10)
- Featured Gov (9)
- Industry Expertise (9)
- AI (8)
- Networking (6)
- Hybrid Cloud (5)
- NIST SP 800-171 (4)
- Reporting (3)
- Services (3)
- Cloud Security (2)
- Copilot for Microsoft 365 (2)
- GDPR (2)
- Pure Storage (2)
- Mobile (1)
- Reporting-as-a-Service (1)